
We have just detected a third FakePlayer SMS Trojan for Android phones – it’s been a month since we saw the second one. What’s new in this one?
First of all, the ‘porno player’ icon from the first variant has returned.

In the second place, this variant sends for-fee SMS/text messages to two short numbers now – 7132 as in the previous version and also 4161 - new for this version.

The cost for every SMS/text message remains 6 USD (about 170 Russian rubles).
There are no other changes. The same archive – pornplayer.apk, the same infection vector – via the Internet using SEO tricks and the same queries upon installation:

So no real changes – just a new variant to earn additional money… But the trend for regular updates is a concern.
PS Everyone with a phone which supports J2ME should also beware: if you go to a website which is spreading Trojan-SMS.AndroidOS.FakePlayer.c using a mobile web browser, such as Opera Mini for instance, you will be offered a link to download J2ME application – which happens to be a Trojan we detect as as Trojan.SMS.J2ME.Small.r.
2010/08/13 - [보안관련소식] - 시만텍(Symantec), 안드로이드 악성코드 "AndroidOS.Tapsnake" 발견
2010/08/10 - [보안관련소식] - 카스퍼스키(Kaspersky), 세계 최초 안드로이드OS SMS 트로이목마 발견
2010/08/04 - [보안관련소식] - 안드로이드(Android), 개인정보를 유출하는 악성코드 "AndroidOS.Ewalls" 발견
'IT 보안소식' 카테고리의 다른 글
| Win32.Parite.B 바이러스 주의 및 전용백신 안내 (13) | 2010.10.17 |
|---|---|
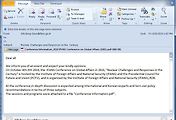
| [SpamMail] "Nuclear Challenges and Responses in the Century" 제목으로 전파 되는 메일 주의!! (0) | 2010.10.15 |
| [SpamMail] "(E-Mail 주소) has sent you a birthday ecard" 제목으로 전파 되는 메일 주의!! (0) | 2010.10.12 |
| 구글 로고(Google Logo), 한글이 창조 된 "한글날 564돌"을 기념하는 로고 (4) | 2010.10.09 |
| 구글 로고(Google Logo), 존 레넌(John Winston Ono Lennon) 70번째 생일 축하기념 (0) | 2010.10.09 |



댓글