해당내용의 원본 주소는 다음과 같다.
http://blog.trendmicro.com/new-exploit-takes-on-ms-powerpoint/
A new 0-day malware leveraging on a vulnerability found in Microsoft PowerPointis making rounds. Distributed as attachment to spam messages, specially crafted PowerPoint files are used for exploitation, which would grant cybercriminals access into the affected user’s system.
Here are screenshots of the said PowerPoint files:
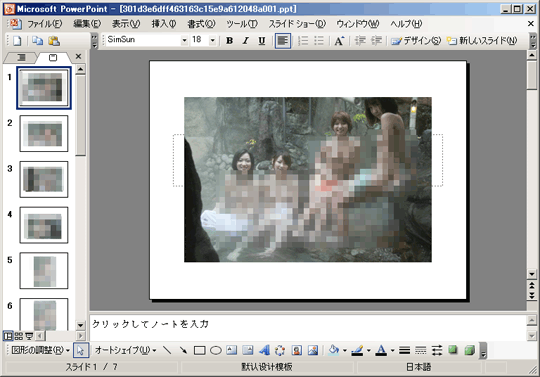
Figure 1. Spammed malicious PPT file

Figure 2. Spammed malicious PPT file

Figure 3. Spammed malicious PPT file
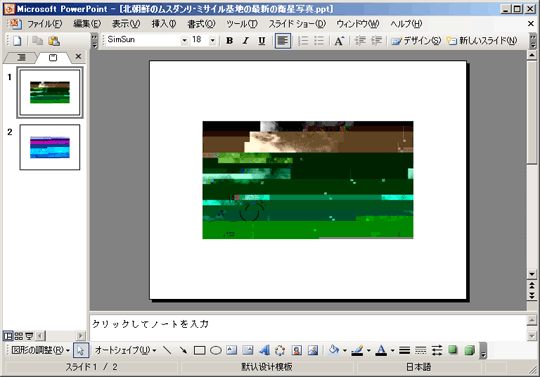
Figure 4. Spammed malicious PPT file
The aforementioned files containing the exploit are detected by Trend Micro as TROJ_PPDROP.AB. According to the analysis of Trend Micro Researcher Michael Cortes, upon successful exploitation, TROJ_PPDROP.AB drops the following files in the affected system’s temporary folder:
- temp.exe – detected as TROJ_KUPS.F
- suhost.exe – detected as BKDR_KUPS.F
TROJ_KUPS.F terminates processes commonly associated with Adobe Reader if found on the system. It also deletes certain registry entries then overwrites the original PowerPoint file with a normal file then executes it, making the user believe that the executed file is non-malicious. It then deletes itself after executing its routines.
On the other hand, BKDR_KUPS.F checks for Internet connection on the affected system by attempting to connect to www.download.windowsupdate.com. Once connection is verified it then connects to a certain IP address to communicate and wait for further commands. It is reported capable of executing the following commands:
- send information such as computer name, IP address and OS version.
- perform a directory search
- list down the contents of the compromised system.
- download an updated copy of itself or another malware
Microsoft already released a security advisory for the vulnerability, and hopefully a fix for it will be available soon. Meanwhile, users are now protected from this threat through the Trend Micro Smart Protection Network.
'IT 보안소식' 카테고리의 다른 글
| 메신저를 통해 전파되는 V.WOM.Messenger.pbe 악성코드 주의 (2) | 2009.04.15 |
|---|---|
| QOOK 광고의 진실(일명 개고생 CF) (0) | 2009.04.07 |
| 2009년 4월 1일 만우절, 유명 사이트들의 "만우절 이벤트" 모음 (2) | 2009.04.01 |
| Google Chrome 2.0 Pre-Beta (0) | 2009.03.31 |
| V3 Internet Security 제품군 윈도우 7 베타지원 (0) | 2009.03.31 |



댓글