
Adobe has released a new Adobe Reader version that contains functionality to block my /Launch action PoC, but Bkis found a bypass: just put double quotes around cmd.exe, like this: “cmd.exe”.
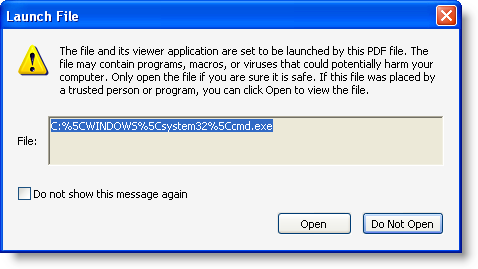
I did some research and discovered that Adobe implemented a blacklist of extensions for the launch action, but that the blacklisting functionality identifies the file type of “cmd.exe” as .exe”, and not .exe
Adobe is aware of the issue, and will evaluate the need to fix the blacklisting functionality.
But meanwhile, you can apply my fix to block launching “cmd.exe”.
You can configure the blacklist of extensions via the registry. Go to HKLM\SOFTWARE\Policies\Adobe\product\version\FeatureLockDown\cDefaultLaunchAttachmentPerms and open registry value tBuiltInPermList.
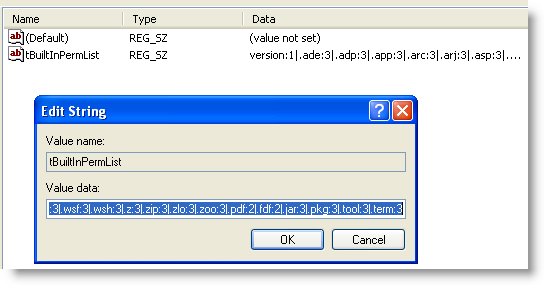
This is a list of |-separated extensions, together with the action Adobe Reader should take (3 means block the extension). Add .exe”:3 to block “cmd.exe”:
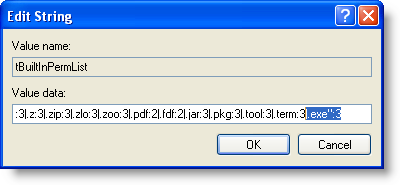
With this addition, Bkis’ bypass will not work anymore:
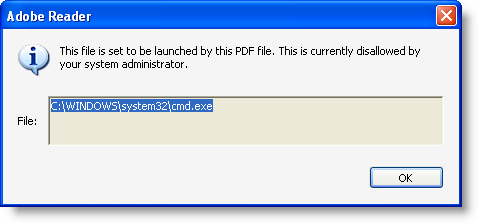
Some further testing shows that adding 2 double quotes is also a way to bypass the blacklist: “”cmd.exe”":
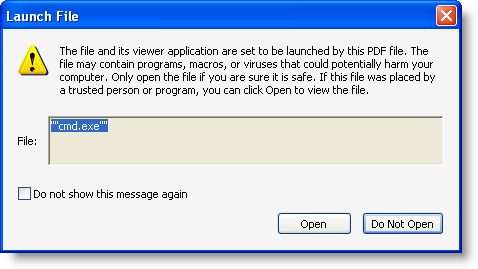
So we need to block this too:

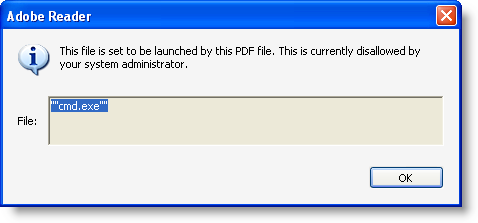
I tested 3 and 4 quotes too, but this is not accepted by Adobe Reader. But should there still be other valid characters to append to the extension, you can block them in the same way as I showed here, until Adobe fixes the blacklist functionality.
2010/06/15 - [악성코드소식] - PDF 프로그램 취약점으로 인한 파일생성(/Launch /Action 명령어 취약점)
2010/04/15 - [보안관련소식] - Adobe PDF 취약점으로 인한 주의(/Launch /Action 명령어)
'IT 보안소식' 카테고리의 다른 글
| 트렌드마이크로(TrendMicro), ZeuS/ZBOT Targets Russian Banks (2) | 2010.07.06 |
|---|---|
| 네이트온 악성코드 사진변경(2010-07-05) (2) | 2010.07.05 |
| 네이트온 악성코드 사진변경(2010-06-28) (2) | 2010.06.28 |
| [SpamMail] "My Husband, My Lover" 제목으로 전파 되는 메일 주의!! (0) | 2010.06.23 |
| BC카드 이용대금 명세서를 가장한 악성코드 분석 (4) | 2010.06.23 |




댓글