Various exploit packs are getting very popular these days. Using them is easy way to infect thousands computers around the world. Each exploit package is composed of several exploits (mostly actual vulnerabilities). Sometimes it is single file which contains all the exploits. More often, each exploit is represented by a different file. This technique seems to be more successful for attack, because antivirus software may detect only part of the exploit pack. The rest of the pack which is still undetected may serve new malware to users. This article describes the structure and activities of one of the more complex exploit pack.
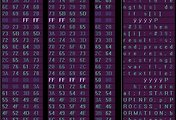
The pack I am writing about was discovered last week on many Chinese servers. As I was writing above, avast! was detecting only part of it so the rest of the detections were released a while after its discovery. It is not really new exploit pack – just a new version of the previously used one. The new version means that creators changed it to achieve lower detection rate by all antivirus software. Its complexity is very high as you can see in the next image – diagram:
This exploit pack contains nearly 40 files including redirectors, vulnerability testers, exploits and shellcodes. As image shows there are two damaged branches. One for PDF exploit (PDF file was damaged – cannot exploit as it cannot be loaded) and one probably for SWF exploit (404 error). Anyway there is still 11 exploits ready to attack. All of them are detected with avast! antivirus. It might be very interesting for the reader to see how other AV engines are dealing with this complex exploit pack. So I have prepared following image with nice colored table (hope you like it):
The table shows which file was detected by what antivirus. Last two columns contain detection rates on full pack and detection rates on exploit files. I am leaving antivirus quality assessment up to the reader choice, but zero detection says everything. GData uses avast! engine in their multiengine scanner – that’s the reason why they are as good as we are.
All data for the table was gathered from virustotal and all the original reports are added to the end of the article to show I am not blaming you with faked results. Let’s see: cqq0.htm (image)(link) |cqq2.css (image)(link) |cqq2s.css (image)(link) |cqqmp.htm (image)(link) |cqqskin.css (image)(link) |cry.css (image)(link) |dvd.js (image)(link) |ec1.htm (image)(link) |ec4.js (image)(link) |ecb.htm (image)(link) |ecbbb.htm (image)(link) |ecfff.js (image)(link) |ecffx.htm (image)(link) |ecfox.htm (image)(link) |ecfox.js (image)(link) |ecof.htm (image)(link) |evilr.htm (image)(link) |evilrr.js (image)(link) |fycry.htm (image)(link) |fydvd.htm (image)(link) |fylz.htm (image)(link) |fyr.htm (image)(link) |fyr1.js (image)(link) |fyre1.htm (image)(link) |google_ad.js (image)(link) |google_ads.js (image)(link) |google_adx.js (image)(link) |music.js (image)(link) |off.css (image)(link) |rr.js (image)(link) |sfpf.htm (image)(link) |show.jpg (image)(link) |shows.jpg (image)(link) |xxxxz.js (image)(link) |zz.js (image)(link) |
'IT 보안소식' 카테고리의 다른 글
| 델파이 개발자를 노리는 Win32.Induc.a 바이러스 확산!! (4) | 2009.08.20 |
|---|---|
| 이스트소프트, MAPP 가입완료 (2) | 2009.08.18 |
| 바이러스체이서 실시간 감시 드라이버 변경 업데이트 (3) | 2009.08.12 |
| [Spammer]동영상 플러그인으로 둔갑한 악성코드 (4) | 2009.08.10 |
| 디도스 공격 한달…‘보안 불감증’ 여전 -kbs (6) | 2009.08.10 |




댓글